Dynamic Multipoint VPN – Dual hub
In a previous article, I exposed how to setup a basic DMVPN network with one hub router in a central location and several spoke routers negotiating a dynamically built IPSec protected GRE tunnel. I also explained the central site should be secured by deploying two hub routers… Here is one solution among others using DMVPN and OSPF. (Should you need another solution you can always contact our professional services)
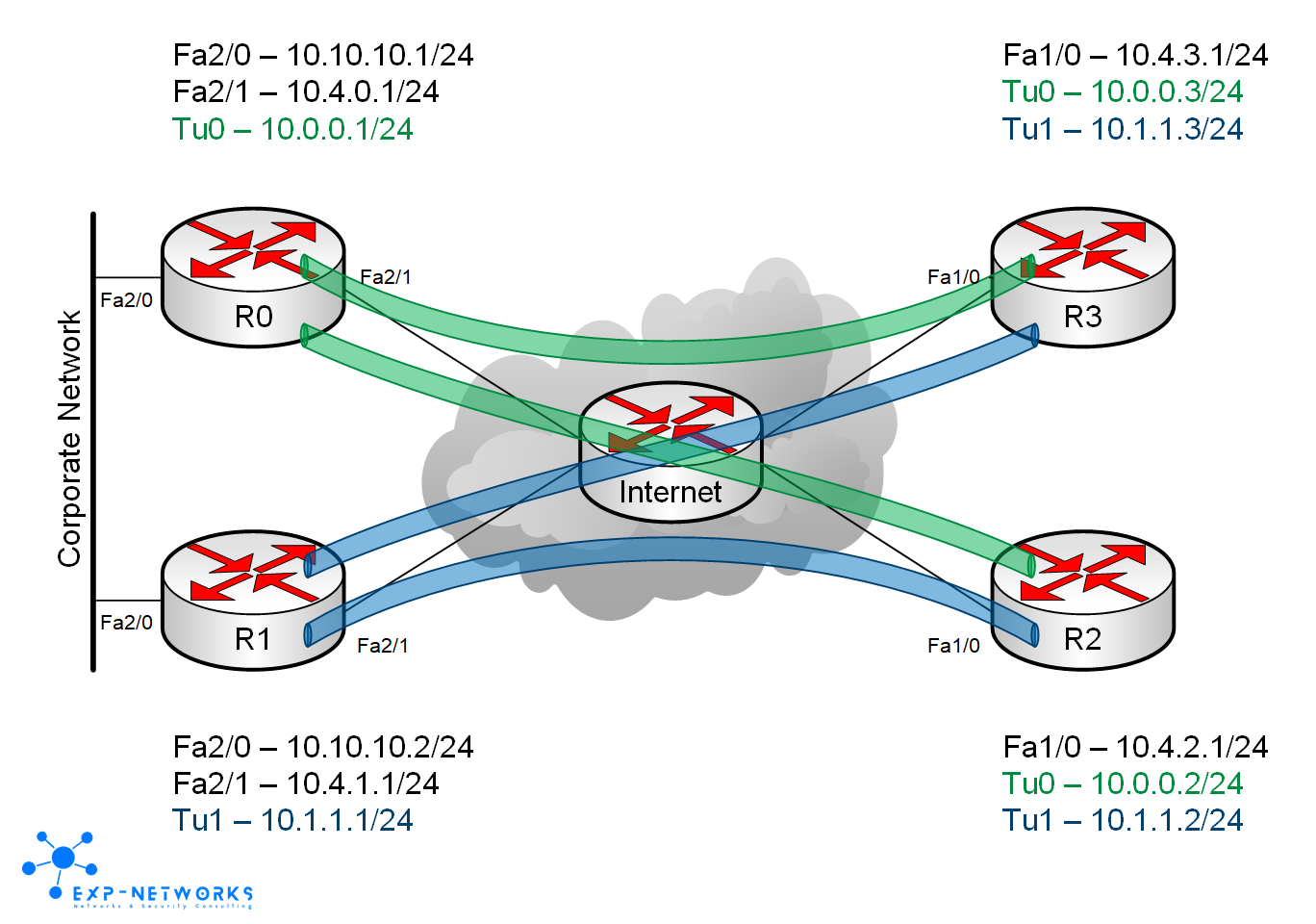
In this scenario, the spoke routers will have two GRE tunnels, one ending on each hub routers.
First we configure the hub routers with mGRE interfaces and OSPF.
The tunnel interfaces use point-to-point OSPF network type by default, we will need to reconfigure them with NBMA OSPF network type as we will have several spoke routers ending their tunnel on them. We will also set the OSPF costs in order to have R0 acting as the preferred hub router and R1 as the backup hub router.
Hub router R0′s config
interface Tunnel0 ip address 10.0.0.1 255.255.255.0 no ip redirects ip nhrp network-id 1 ip ospf network non-broadcast ip ospf cost 10 tunnel source FastEthernet2/1 tunnel mode gre multipoint tunnel key 1 ! interface FastEthernet2/0 ip address 10.10.10.1 255.255.255.0 ! interface FastEthernet2/1 ip address 10.4.0.1 255.255.255.0 ! router ospf 1 log-adjacency-changes network 10.0.0.0 0.0.0.255 area 10 network 10.10.10.0 0.0.0.255 area 10 ! ip route 0.0.0.0 0.0.0.0 10.4.0.2
Hub router R0′s config
interface Tunnel1 ip address 10.1.1.1 255.255.255.0 no ip redirects ip nhrp network-id 1 ip ospf network non-broadcast ip ospf cost 100 tunnel source FastEthernet2/1 tunnel mode gre multipoint tunnel key 1 ! interface FastEthernet2/0 ip address 10.10.10.2 255.255.255.0 ! interface FastEthernet2/1 ip address 10.4.1.1 255.255.255.0 ! router ospf 1 log-adjacency-changes network 10.0.0.0 0.0.0.255 area 10 network 10.10.10.0 0.0.0.255 area 10 ! ip route 0.0.0.0 0.0.0.0 10.4.1.2
Then we can start to add spoke routers. The spoke routers will use point-to-point GRE (as we don’t want spoke-to-spoke direct communication) with NBMA OSPF network type in order to be compatible with the hub routers’ settings. We also need to define the neighbors as we’re on an NBMA network. I’ve chosen to do that on the spoke routers as ì don’t want to have to touch the hub routers config when new spoke routers are added.
Spoke router R2′s config
interface Loopback0 ip address 2.2.2.2 255.255.255.255 ! interface Tunnel0 ip address 10.0.0.2 255.255.255.0 ip nhrp map 10.0.0.1 10.4.0.1 ip nhrp network-id 1 ip nhrp nhs 10.0.0.1 ip ospf network non-broadcast ip ospf cost 10 ip ospf priority 0 tunnel source FastEthernet1/0 tunnel destination 10.4.0.1 tunnel key 1 ! interface Tunnel1 ip address 10.1.1.2 255.255.255.0 ip nhrp map 10.1.1.1 10.4.1.1 ip nhrp network-id 1 ip nhrp nhs 10.1.1.1 ip ospf network non-broadcast ip ospf cost 100 ip ospf priority 0 tunnel source FastEthernet1/0 tunnel destination 10.4.1.1 tunnel key 1 ! interface FastEthernet1/0 ip address 10.4.2.1 255.255.255.0 ! router ospf 1 log-adjacency-changes network 2.2.2.2 0.0.0.0 area 10 network 10.0.0.0 0.0.0.255 area 10 network 10.1.1.0 0.0.0.255 area 10 neighbor 10.0.0.1 neighbor 10.1.1.1 ! ip route 0.0.0.0 0.0.0.0 10.4.2.2
Same config is applied on spoke router R3, only the IP change.
To check the GRE tunnels are operational, we only have to ping the tunnels’ internal IP from one router to the others three.
From spoke router R2 :
R2#ping 10.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 8/8/8 ms R2#ping 10.1.1.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.3, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 16/17/24 ms R2#ping 10.0.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 8/11/24 ms R2#ping 10.0.0.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 16/20/32 ms
If we check the NHRP entries on the hubs R0 or R1, we can see the two entries have been learned dynamically and the public IP used by the remote routers.
R1#sh ip nhrp 10.1.1.2/32 via 10.1.1.2, Tunnel1 created 02:08:37, expire 01:38:57 Type: dynamic, Flags: authoritative unique registered used NBMA address: 10.4.2.1 10.1.1.3/32 via 10.1.1.3, Tunnel1 created 02:08:36, expire 01:38:57 Type: dynamic, Flags: authoritative unique registered used NBMA address: 10.4.3.1 R0#sh ip nhrp 10.0.0.2/32 via 10.0.0.2, Tunnel0 created 02:15:15, expire 01:53:44 Type: dynamic, Flags: authoritative unique registered NBMA address: 10.4.2.1 10.0.0.3/32 via 10.0.0.3, Tunnel0 created 02:11:04, expire 01:53:44 Type: dynamic, Flags: authoritative unique registered NBMA address: 10.4.3.1
Now, check OSPF is doing what we want. First we check the ospf neighbors on spoke router R2
R2#sh ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 10.10.10.2 1 FULL/DR 00:01:54 10.1.1.1 Tunnel1 10.10.10.1 1 FULL/DR 00:01:55 10.0.0.1 Tunnel0
Then we can check corporate subnet 10.10.10.0/24 and other spokes (here R3′s Loopback 3.3.3.3) are reachable via the primary hub router R0.
R2#sh ip route ospf
3.0.0.0/32 is subnetted, 1 subnets
O 3.3.3.3 [110/11] via 10.0.0.3, 00:42:46, Tunnel0
10.0.0.0/24 is subnetted, 4 subnets
O 10.10.10.0 [110/11] via 10.0.0.1, 00:42:46, Tunnel0
On the hub routers we can check the spoke routers are always reached via R0.
R0#sh ip route ospf
2.0.0.0/32 is subnetted, 1 subnets
O 2.2.2.2 [110/11] via 10.0.0.2, 00:49:41, Tunnel0
3.0.0.0/32 is subnetted, 1 subnets
O 3.3.3.3 [110/11] via 10.0.0.3, 00:49:41, Tunnel0
10.0.0.0/24 is subnetted, 4 subnets
O 10.1.1.0 [110/101] via 10.10.10.2, 00:49:41, FastEthernet2/0
R1#sh ip route ospf
2.0.0.0/32 is subnetted, 1 subnets
O 2.2.2.2 [110/12] via 10.10.10.1, 00:50:52, FastEthernet2/0
3.0.0.0/32 is subnetted, 1 subnets
O 3.3.3.3 [110/12] via 10.10.10.1, 00:50:52, FastEthernet2/0
10.0.0.0/24 is subnetted, 4 subnets
O 10.0.0.0 [110/11] via 10.10.10.1, 00:50:52, FastEthernet2/0Now that we have IP connectivity, we can enable IPSec exactly as we did last time.
crypto isakmp policy 10 authentication pre-share crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0 ! crypto ipsec transform-set mySet esp-aes esp-sha-hmac ! crypto ipsec profile myDMVPN set security-association lifetime seconds 120 set transform-set mySet set pfs group2 interface Tunnel0 tunnel protection ipsec profile myDMVPN interface Tunnel1 tunnel protection ipsec profile myDMVPN
That’s all folks! Now we have a DMVPN setup with redundant hub routers…